Cybersecurity Compliance
NIST 800-53 compliance
NIST 800-53, titled “Security and Privacy Controls for Information Systems and Organizations,” is a critical cybersecurity framework developed by the National Institute of Standards and Technology (NIST). It provides over 1,000 controls such as Access Control and Incident Response Management, to protect federal information systems. Mandatory for U.S. federal agencies under FISMA, its Revision 5 (published in 2020) combines privacy controls, addressing modern challenges like cloud computing and insider threats.
The framework’s strength lies in its scalability and flexibility, offering customizable control baselines (low, moderate, high impact) that suit organizations of all sizes. It aligns with NIST’s Risk Management Framework (RMF) for proactive threat mitigation and is widely adopted by private sectors to bolster cybersecurity. NIST 800-53 ensures confidentiality, integrity, and availability while protecting personally identifiable information (PII) through tailored technical, operational, and management controls.
To implement NIST 800-53, organizations identify system impact levels, select appropriate controls, customize them, and continuously monitor effectiveness. Ideal for federal agencies, contractors, and private entities, it’s a robust standard for enhancing security posture. For more details, visit NIST SP 800-53.
FISMA compliance
The Federal Information Security Management Act (FISMA) is a U.S. law designed to protect government information and systems by setting cybersecurity standards for federal agencies and their contractors. FISMA compliance ensures the confidentiality, integrity, and availability of sensitive federal data through risk management, continuous monitoring, and adherence to NIST guidelines. FISMA compliance is critical not only to meet legal requirements but also to build trust with government partners and avoid penalties like fines or contract loss.
To achieve FISMA compliance, organizations must categorize systems based on data sensitivity (using NIST 800-60), implement appropriate NIST 800-53 security controls, and conduct regular audits to ensure effectiveness. This involves creating System Security Plans (SSPs), maintaining Plans of Action and Milestones (POA&Ms), and obtaining an Authority to Operate (ATO). Continuous monitoring and robust incident response plans are also essential to address threats. Using automated tools and training staff can streamline the process of staying compliant. By prioritizing FISMA compliance, organizations safeguard data and strengthen their credibility in handling federal contracts.
STIG
Security Technical Implementation Guides (STIGs) are configuration standards developed by the Defense Information Systems Agency (DISA) to secure systems and software used by the U.S. Department of Defense (DoD) and other federal entities. These detailed guidelines help organizations reduce vulnerabilities and protect sensitive data from cyber threats.
STIGs provide specific, actionable instructions to harden IT systems, applications, and networks against attacks. They cover a wide range of technologies, from operating systems like Windows and Linux to databases and network devices. Each STIG includes security controls, configuration settings, and best practices tailored to mitigate risks, such as unauthorized access or data breaches. Compliance with STIGs is mandatory for DoD systems and often required for contractors handling federal data. Non-compliance can lead to system vulnerabilities, failed audits, or loss of partnership.
Achieving STIG compliance involves identifying applicable STIGs for your systems, applying the recommended configurations, and documenting compliance through tools like the Security Content Automation Protocol (SCAP). Regular audits and continuous monitoring ensure settings remain secure. While STIG implementation can be complex due to the volume of requirements, automation tools and scripts can simplify the process. By adhering to STIGs, organizations strengthen their cybersecurity posture, meet federal requirements, and build trust with government partners.
ISO 27001
ISO 27001 is an internationally recognized standard for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). Published by the International Organization for Standardization (ISO), it provides a framework for organizations to manage and protect sensitive information, ensuring confidentiality, integrity, and availability. This short blog explores the essentials of ISO 27001 and its value.
The standard outlines a risk-based approach to cybersecurity, requiring organizations to identify threats, assess risks, and implement controls from a comprehensive set outlined in Annex A. These controls cover areas like access management, encryption, incident response, and employee training. Achieving ISO 27001 certification demonstrates a commitment to robust security practices, enhancing trust with clients. It’s particularly valuable for organizations handling sensitive data, such as financial institutions or healthcare providers.
Implementing ISO 27001 involves defining the ISMS scope, conducting risk assessments, selecting appropriate controls, and undergoing an external audit for certification. Continuous monitoring and regular reviews ensure ongoing compliance. While the process can be resource-intensive, tools like risk management software and expert consultants can streamline efforts. By adopting ISO 27001, organizations not only mitigate cyber risks but also build a culture of security, fostering resilience and credibility in a data-driven world.
SOC
Service Organization Control (SOC) compliance is a framework developed by the American Institute of Certified Public Accountants (AICPA) to ensure service providers securely manage client data. SOC reports (SOC 1, SOC 2, and SOC 3) help organizations demonstrate robust controls over financial reporting, security, availability, confidentiality, processing integrity, and privacy. This brief blog covers the essentials of SOC compliance and its importance.
SOC 1 focuses on financial reporting controls, while SOC 2 addresses security and operational controls based on the Trust Services Criteria, making it critical for technology and cloud service providers. SOC 3 is a simplified, public-facing report for broader use. Achieving SOC compliance involves assessing risks, implementing controls, and undergoing independent audits by CPA firms.
The process of compliance requires defining the scope of systems, documenting policies, and testing controls over time (Type II reports evaluate effectiveness over a period). Challenges include resource demands and maintaining continuous compliance. Automation tools and expert consultants can streamline audits and monitoring. By achieving SOC compliance, organizations enhance credibility, reduce risks, and gain a competitive edge in industries where data security is paramount.
Infrastructure Security Design Concepts
Defense in Depth
As cyber threats become more sophisticated over past years, organizations prioritize robust security strategies to safeguard their assets. Defense in Depth is a proven cybersecurity framework that employs multiple layers of protection to ensure no single failure compromises the entire system. This approach creates overlapping defenses to deter, delay, or detect attackers. By making attacks more complex and time-consuming, Defense in Depth significantly reduces the risk of a breach.
The importance of Defense in Depth comes in its ability to address different nature of cyber threats, from malware to insider threats and advanced persistent threats (APTs). Relying on a single security measure, such as a firewall, is insufficient against today’s complex cyber-attacks. Defense in Depth mitigates risks by eliminating single points of failure, increasing the effort required for a successful attack, and providing security teams with critical time to respond.
Implementing Defense in Depth involves multiple layers, each targeting specific vulnerabilities. Physical security ensures that servers and devices are protected from unauthorized access through measures like biometric locks and surveillance. Network security employs firewalls, intrusion detection systems, VPNs, and network segmentation to secure both the perimeter and internal traffic. Lastly, endpoint security safeguards laptops and computers with managing antivirus software and regular updates. By combining these layers, organizations create a resilient defense that adapts to the continuous changing threats.
Zero Trust Security Model
In today’s rapidly evolving cyber world, traditional security models that assume trust within a network are no longer sufficient. The Zero Trust security model revolutionizes cybersecurity by operating on a simple principle: never trust, always verify. This approach assumes that no user, device, or system inside or outside the network can be trusted inherently, requiring continuous authentication and authorization to prevent breaches.
Zero Trust is critical in our era of remote work, cloud computing, and sophisticated threats like ransomware and insider attacks. Zero Trust mitigates these risks by eliminating implicit trust, reducing the attack surface, and ensuring that even compromised credentials don’t grant any access. It’s a proactive strategy designed for a complex cyber world.
Implementing Zero Trust involves key practices: Identify verification that ensures every user and device is authenticated using multi-factor authentication (MFA). Least privilege access grants users only the permissions they need, minimizing potential damage. Continuous monitoring tracks behavior and network activity to detect anomalies in real time. Adopting these principles can help organizations build a robust, adaptive security posture that protects against modern threats.
Information Security Frameworks
Cybersecurity Framework (CSF)
The Cybersecurity Framework (CSF), developed by the National Institute of Standards and Technology (NIST), is a voluntary set of guidelines designed to help organizations manage and reduce cybersecurity risks. Updated in 2024 with CSF 2.0, it provides a structured approach through five core functions: Identify, Protect, Detect, Respond, and Recover. These functions create a cycle for assessing risks, safeguarding assets, monitoring threats, addressing incidents, and restoring operations, making it adaptable for organizations of all sizes and sectors.
CSF 2.0 emphasizes governance as a sixth function, pointing the importance of integrating cybersecurity into organizational leadership and decision-making. It offers a flexible framework that aligns with business objectives, allowing customization based on specific needs, risk tolerance, and resources. By using profiles and tiers, organizations can prioritize actions, measure progress, and align their cybersecurity practices with industry standards, fostering resilience against evolving threats like ransomware and supply chain attacks.
Adopting the CSF can enhance an organization’s ability to communicate cybersecurity priorities internally and with external partners. Its widespread use across industries promotes consistency, enabling better collaboration and information sharing. As cyber threats grow in complexity, the CSF remains a vital tool for building robust defenses, ensuring organizations can adapt to new challenges while maintaining trust and operational continuity.
MITRE ATT&CK Framework
The MITRE ATT&CK Framework is a globally recognized knowledge base of adversary tactics, techniques, and procedures (TTPs) used to understand and defend against cyber threats. Developed by MITRE in 2013, ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) organizes cyberattack behaviors into a structured matrix, covering enterprise, cloud, and mobile environments. It categorizes tactics like initial access, persistence, and exfiltration, detailing specific techniques attackers use.
The framework’s strength is its detailed real-world applicability, drawing from observed attacks to provide actionable solutions. Organizations use ATT&CK to map adversary behaviors, assess vulnerabilities, and prioritize defenses. By aligning security operations with its matrix, teams can improve threat detection, incident response, and threat hunting, tailoring strategies to specific threat actors or campaigns, such as ransomware or advanced persistent threats (APTs).
ATT&CK also promote collaboration by offering a common language for sharing threat intelligence across industries. Its open-source nature ensures continuous updates, reflecting the latest attack trends. As cyber threats evolve, the MITRE ATT&CK Framework remains a cornerstone for building proactive, intelligence-driven cybersecurity programs, empowering organizations to stay ahead of sophisticated adversaries.
Diamon Model of Intrusion
The Diamond Model of Intrusion Analysis, developed in 2013, is a framework designed to analyze and understand cyber intrusions comprehensively. It structures an attack into four core components—adversary, infrastructure, capability, and victim—forming a “diamond” that captures the relationships between these elements. By mapping these components, the model helps analysts dissect malicious activities, identify patterns, and attribute attacks to specific threat actors, making it a powerful tool for threat intelligence and incident response.
At its core, the Diamond Model emphasizes association between an adversary’s goals and their technical methods. Adversaries exploit infrastructure (e.g., command-and-control servers) and capabilities (e.g., malware or exploits) to target victims, such as organizations or individuals. Analysts can use the model to pivot across these elements, uncovering details like the tools used, the attacker’s intent, or the compromised systems. This relational approach enables organizations to move beyond isolated indicators of compromise (IoCs) and build a holistic view of an attack.
The model’s flexibility makes it valuable across industries, supporting threat hunting, attribution, and defense strategy development. By integrating with frameworks like MITRE ATT&CK, it enhances the ability to contextualize and prioritize threats. As cyber threats grow in sophistication, the Diamond Model remains a critical framework for understanding intrusions, enabling organizations to strengthen defenses and disrupt adversary operations effectively.
Cyber Kill Chain
The Cyber Kill Chain, developed by Lockheed Martin in 2011, is a framework that outlines the stages of a cyberattack, providing a structured approach to understanding and defending against threats. It consists of seven phases: Reconnaissance, Weaponization, Delivery, Exploitation, Installation, Command and Control, and Actions on Objectives. By breaking down an attack into these steps, the model helps organizations identify vulnerabilities and disrupt malicious activities at various points, enhancing proactive cybersecurity measures.
Each phase of the Cyber Kill Chain represents a critical point where defenders can intervene. For example, during Reconnaissance, attackers gather information about their target, which defenders can counter by limiting publicly available data. In later stages, such as Exploitation or Command and Control, robust endpoint protection and network monitoring can block malicious payloads or detect unusual communications. This phased approach enables security teams to prioritize resources, tailor defenses, and mitigate risks before attackers achieve their goals, such as data theft or system disruption.
Widely adopted across industries, the Cyber Kill Chain fosters a shared understanding of attack progression, aiding collaboration between security teams and threat intelligence sharing. While it may not capture every modern attack vector, such as insider threats, its structured methodology remains a cornerstone for building layered defenses. By integrating the Kill Chain with other frameworks like MITRE ATT&CK, organizations can strengthen their ability to anticipate, detect, and respond to evolving cyber threats effectively.
Staying Updated With Latest Threats
CISA Advisories
The Cybersecurity and Infrastructure Security Agency (CISA) plays a role in safeguarding critical infrastructure by issuing timely advisories that alert cybersecurity professionals to emerging cyber threats. These advisories provide detailed insights into vulnerabilities, exploits, and attack trends, often including actionable recommendations for mitigation. By gathering intelligence from government, industry, and global partners, CISA ensures that its advisories reflect the latest developments in the threat landscape, enabling professionals to prioritize their defenses effectively.
CISA advisories are a cornerstone for staying updated because they offer both technical depth and practical guidance. For instance, advisories often detail specific vulnerabilities in widely used software, such as zero-day exploits or misconfigurations, alongside steps for patching or workarounds. They also highlight tactics, techniques, and procedures (TTPs) used by threat actors, helping security teams anticipate and counter attacks. This blend of real-time intelligence and prescriptive advice empowers professionals to strengthen their organizations’ security posture proactively.
Beyond immediate threat response, CISA advisories empower a culture of continuous learning and collaboration within the cybersecurity community. By subscribing to alerts or reviewing CISA’s resources, professionals gain access to a wealth of knowledge that supports long-term resilience. These advisories also encourage information sharing across sectors, amplifying collective defense efforts. For cybersecurity professionals, staying engaged with CISA’s updates is not just about reacting to threats—it’s about building a proactive, informed approach to securing the digital landscape.
darkreading.com
DarkReading.com serves as a vital resource for cybersecurity professionals, delivering a steady stream of news, analysis, and insights on the latest cyber threats, vulnerabilities, and industry trends. Through daily or weekly newsletters, the platform ensures professionals receive updates on critical topics like data breaches, emerging attack vectors, and advancements in security technology. By streaming content from global sources and expert contributors, Dark Reading keeps its audience informed about the evolving threat landscape, helping them stay proactive in defending their organizations.
The platform’s in-depth features, such as podcasts like Dark Reading Confidential and detailed reports from events like Black Hat, provide cybersecurity professionals with nuanced perspectives on pressing issues. For example, discussions on the future of the CVE Program or AI’s role in security operations offer strategic insights that go beyond surface-level news. Additionally, Dark Reading’s coverage of specific threats, like the Charon ransomware or APT-style campaigns, equips professionals with actionable intelligence on attacker tactics, techniques, and procedures (TTPs), enabling better preparedness and response.
Beyond news, Dark Reading fosters a sense of community and continuous learning through its Startup Spotlight series and in-depth technology analysis. By highlighting and exploring trends like passwordless authentication risks, the platform helps professionals anticipate future challenges and adopt cutting-edge solutions. With its blend of breaking news, expert commentary, and forward-looking content, DarkReading.com remains an essential tool for cybersecurity professionals striving to stay ahead in a rapidly changing digital world.
Common Vulnerability Exposures (CVE)
Common Vulnerability Exposures (CVE) is a standardized system for identifying and cataloging software vulnerabilities, providing cybersecurity professionals with a universal reference to track and address security flaws. Managed by MITRE and supported by the Cybersecurity and Infrastructure Security Agency (CISA), CVEs assign unique identifiers to vulnerabilities, detailing affected software, severity, and potential impacts. This structured approach enables professionals to quickly understand and prioritize threats, ensuring they stay informed about the latest risks in an ever-evolving digital landscape.
CVEs help cybersecurity teams stay proactive by integrating with tools like vulnerability scanners and threat intelligence platforms, which rely on CVE data to detect and mitigate risks in real time. For example, a newly disclosed CVE for a widely used application can trigger immediate patch management or workaround implementation, reducing the window of exposure. By providing detailed descriptions and references to patches or advisories, CVEs empower professionals to align their defenses with the latest known vulnerabilities, often before attackers can exploit them.
Beyond immediate response, CVEs foster collaboration and knowledge sharing across the cybersecurity community. Publicly accessible databases, such as the National Vulnerability Database (NVD), enrich CVE entries with severity scores and exploitability metrics, helping professionals assess risk efficiently. By staying engaged with CVE updates through feeds, alerts, or industry reports, cybersecurity professionals can maintain a proactive stance, anticipate emerging threats, and contribute to a collective defense against cyberattacks.
AI and Machine Learning
Model Context Protocol
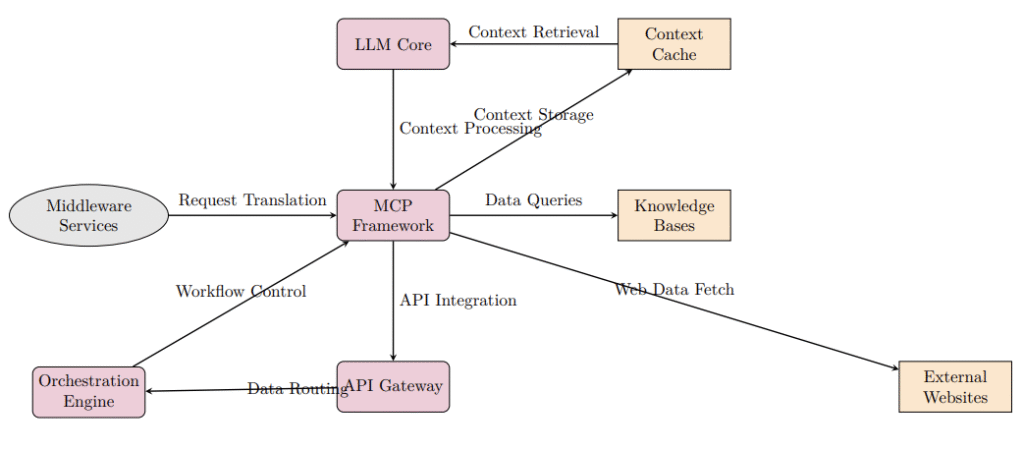
The Model Context Protocol (MCP) is a framework that standardizes how Large Language Models (LLMs) interact with external systems via APIs. It acts as a structured bridge, helping LLMs maintain context across conversations or tasks, ensuring smooth data exchange with applications like real-time systems or workflows. MCP’s rules enable LLMs to process API inputs accurately, making it vital for AI-driven organizations.
MCP creation starts with an LLM’s ability to understand and generate language. Developers define how the LLM handles API inputs, stores context, produces outputs, and tune it for specific domains like e-commerce or healthcare. The LLM is then linked to APIs following MCP standards and contexts, with testing to ensure it handles complex cases and maintains context over time.
MCP uses middleware to translate API calls for the LLM and an orchestration layer to manage data flow between systems. Tools like RESTful APIs or GraphQL ensure compatibility, while MCP’s design supports error handling and scalability. This ensures LLMs for having a power intelligent and context-aware systems that automate complex tasks efficiently.